What is EtherHiding? Google flags malware with crypto-stealing code in smart contracts
North Korean hackers have adopted a method of deploying malware designed to steal crypto and sensitive information by embedding malicious code into smart contracts on public blockchain networks, according to Google’s Threat Intelligence Group.
The technique, called “EtherHiding,” emerged in 2023 and is typically used in conjunction with social engineering techniques, such as reaching out to victims with fake employment offers and high-profile interviews, directing users to malicious websites or links, according to Google.
Hackers will take control of a legitimate website address through a Loader Script and embed JavaScript code into the website, triggering a separate malicious code package in a smart contract designed to steal funds and data once the user interacts with the compromised site.
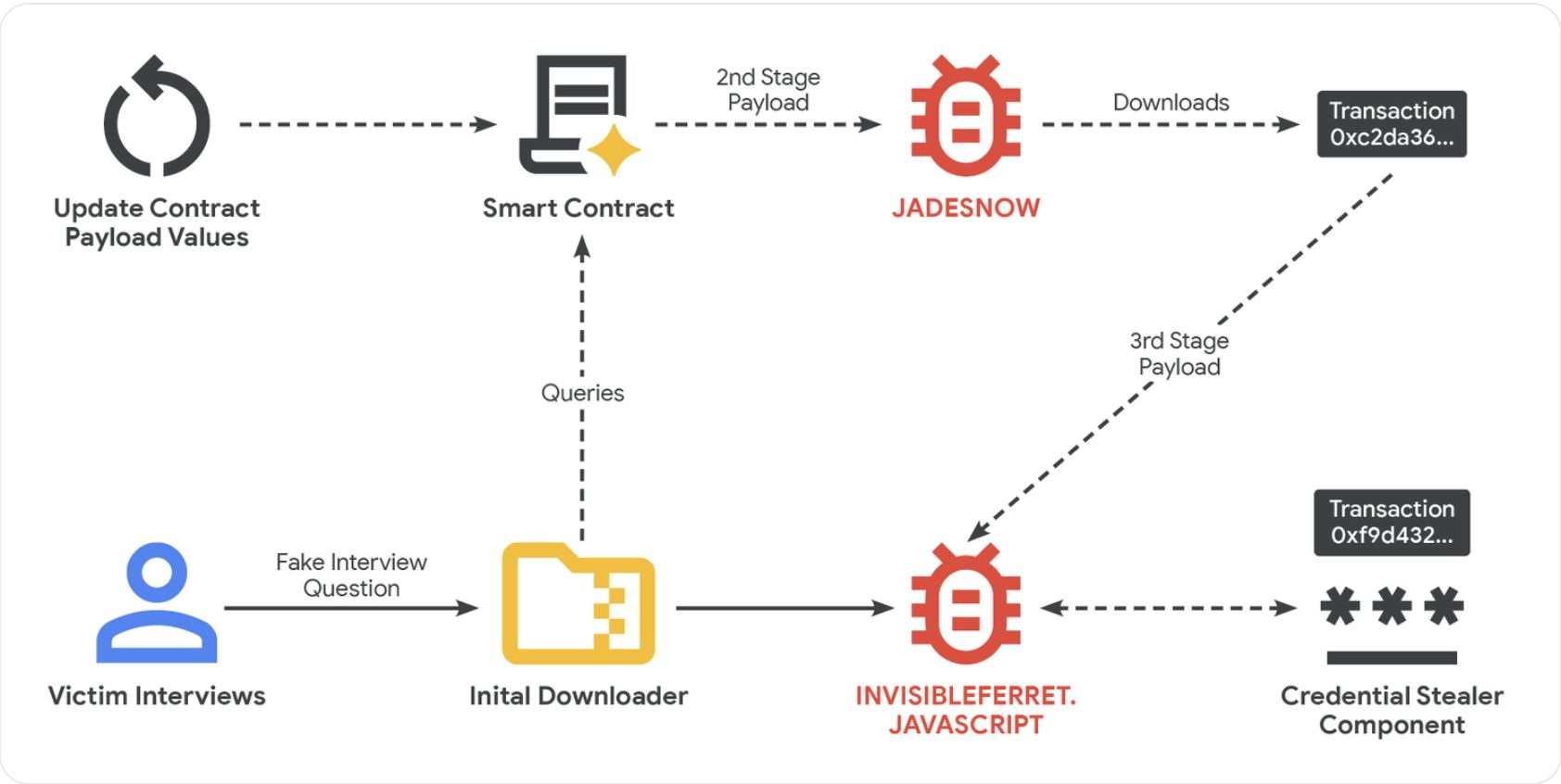
The compromised website will communicate with the blockchain network using a “read-only” function that does not actually create a transaction on the ledger, allowing the threat actors to avoid detection and minimize transaction fees, Google researchers said.
The report highlights the need for vigilance in the crypto community to keep users safe from scams and hacks commonly employed by threat actors attempting to steal funds and valuable information from individuals and organizations alike.
Related: CZ’s Google account targeted by ‘government-backed’ hackers
Know the signs: North Korea social engineering campaign decoded
The threat actors will set up fake companies, recruitment agencies and profiles to target software and cryptocurrency developers with fake employment offers, according to Google.
After the initial pitch, the attackers move the communication to messaging platforms like Discord or Telegram and direct the victim to take an employment test or complete a coding task.
“The core of the attack occurs during a technical assessment phase,” Google Threat Intelligence said. During this phase, the victim is typically told to download malicious files from online code repositories like GitHub, where the malicious payload is stored.
In other instances, the attackers lure the victim into a video call, where a fake error message is displayed to the user, prompting them to download a patch to fix the error. This software patch also contains malicious code.
Once the malicious software is installed on a machine, second-stage JavaScript-based malware called “JADESNOW” is deployed to steal sensitive data.
A third stage is sometimes deployed for high-value targets, allowing the attackers long-term access to a compromised machine and other systems connected to its network, Google warned.
Magazine: Inside a 30,000 phone bot farm stealing crypto airdrops from real users
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Hyperliquid (HYPE) Price Rally: The Role of DeFi Advancements and Investor Sentiment in Driving Recent Market Fluctuations
- Hyperliquid (HYPE) surged to $59.39 in 2025 before retreating, driven by DeFi innovations and volatile market sentiment. - Technical advancements like HyperBFT consensus and USDH stablecoin attracted 73% of decentralized trading volume, while institutional partnerships stabilized the ecosystem. - Despite short-term volatility near $36, bullish RSI patterns and $3 trillion trading volume suggest potential for a $59 rebound, though sustained momentum above $43 is critical. - Analysts project HYPE could rea

The Driving Forces Behind Economic Growth in Webster, NY
- Webster , NY, transformed a 300-acre Xerox brownfield into a high-tech industrial hub via a $9.8M FAST NY grant, boosting industrial and real estate growth. - Public-private partnerships enabled infrastructure upgrades, attracting $650M fairlife® dairy projects and 250 high-paying jobs by 2025. - Industrial vacancy rates dropped to 2%, while residential values rose 10.1% annually, highlighting synergies between infrastructure and economic development. - The model underscores secondary markets' potential

Unlocking Potential: The Impact of Targeted Grants and Public-Private Partnerships on Transforming Medium-Sized Real Estate Markets in the U.S.
- U.S. mid-sized cities leverage infrastructure investment and PPPs to drive commercial real estate growth, outpacing large cities in value creation. - Federal programs like IIJA enable upgrades in transportation and broadband, reducing business costs while boosting property values in Tampa and Grand Rapids. - PPPs in cities like Montgomery County combine affordable housing incentives with CRE development, balancing equity and economic resilience through data-driven strategies. - Market projections show $2
Modern Monetary Theory and the Transformation of International Markets: Inflation Trends, Asset Movements, and Currency Shifts in 2025
- Modern Monetary Theory (MMT) reshapes fiscal-monetary coordination, linking government spending to inflation and resource constraints in post-pandemic economies. - Central banks face challenges anchoring inflation expectations as CPI lags asset market pressures, risking self-fulfilling inflationary spirals amid eroding public trust. - Currency valuations shift with fiscal stimulus (e.g., euro's 2025 rebound) and U.S. dollar uncertainty, compounded by gold reserve diversification and rising bond yields. -

