Someone counter-hacked a North Korean IT worker: Here’s what they found
A small team of North Korean IT workers — linked to a $680,000 crypto hack in June — have been using Google products and even renting computers to infiltrate crypto projects, according to newly leaked screenshots coming from one of the workers’ devices.
In an X post from ZachXBT on Wednesday, the crypto sleuth shared a rare inside look into the workings of a North Korean (DPRK) hacker. The information came from “an unnamed source” who was able to compromise one of their devices.
North Korean-linked workers were responsible for $1.4 billion exploit of crypto exchange Bitbit in February and have siphoned millions from crypto protocols over the years.
The data shows that the small team of six North Korean IT workers shares at least 31 fake identities, obtaining everything from government IDs and phone numbers to purchasing LinkedIn and UpWork accounts to mask their true identities and land crypto jobs.
One of the workers supposedly interviewed for a full-stack engineer position at Polygon Labs, while other evidence showed scripted interview responses in which they claimed to have experience at NFT marketplace OpenSea and blockchain oracle provider Chainlink.
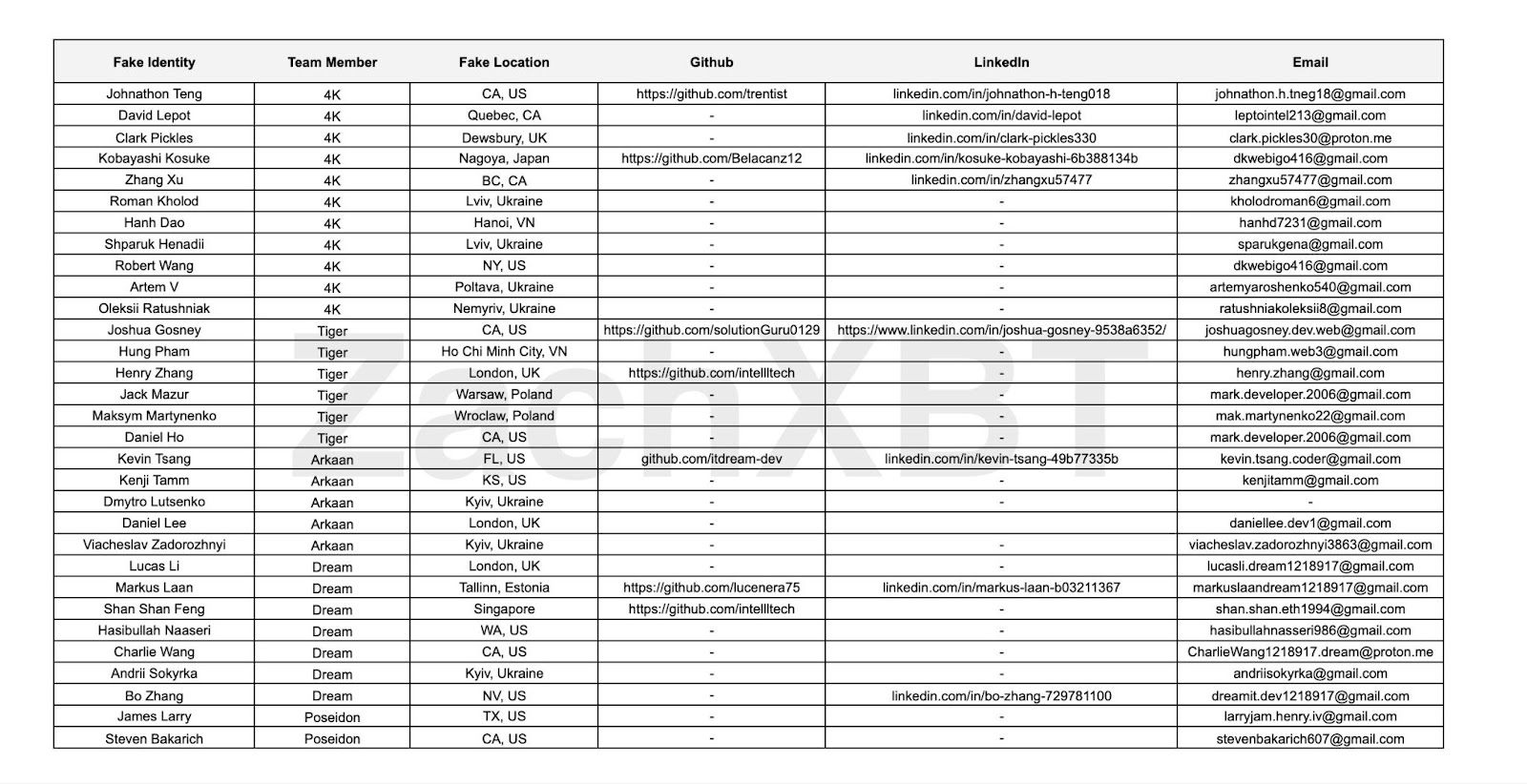 Fake list of identities involved in the North Korean IT scam operation. Source: ZachXBT
Fake list of identities involved in the North Korean IT scam operation. Source: ZachXBT
Google, remote working software
The leaked documents show the North Korean IT workers secured “blockchain developer” and “smart contract engineer” roles on freelance platforms like Upwork, then use remote access software like AnyDesk to carry out the work for unsuspecting employers. They also use VPNs to hide their true location.
Google Drive exports and Chrome profiles show they used Google tools to manage schedules, tasks and budgets, communicating mainly in English while using Google’s Korean-to-English translation tool.One spreadsheet shows IT workers spent a combined $1,489.8 on expenses in May to carry out their operations.
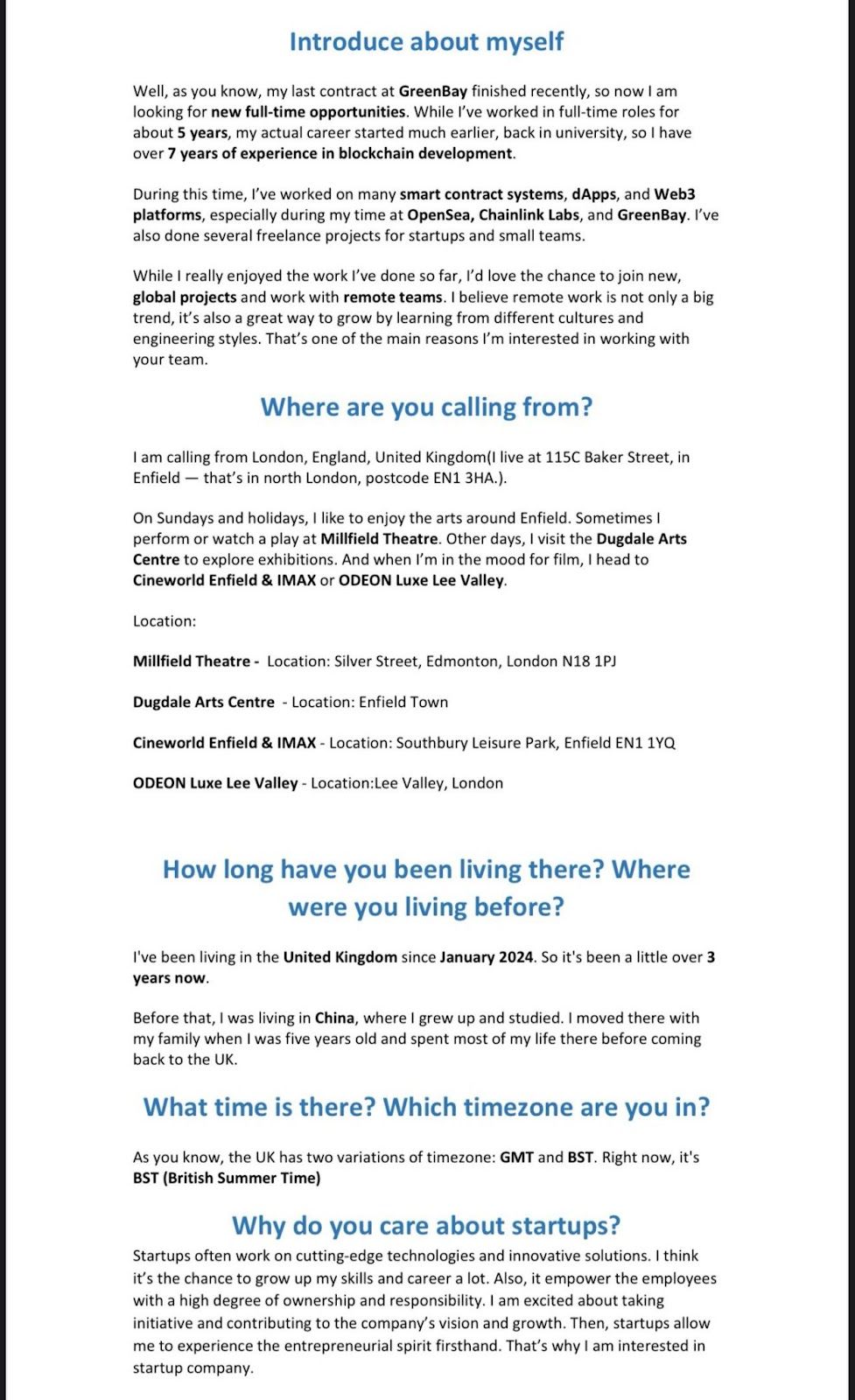 Interview notes/preparation, likely intended to be referenced during an interview. Source: ZachXBT
Interview notes/preparation, likely intended to be referenced during an interview. Source: ZachXBT
North Korean IT workers tied to recent $680,000 crypto hack
The North Koreans often use Payoneer to convert fiat into crypto for their work, and one of those wallet addresses —“0x78e1a” — is “closely tied” to the $680,000 exploit on fan-token marketplace Favrr in June 2025, ZachXBT said.
At the time, ZachXBT alleged the project’s chief technology officer, known as “Alex Hong,” along with other developers, were actually DPRK workers in disguise.
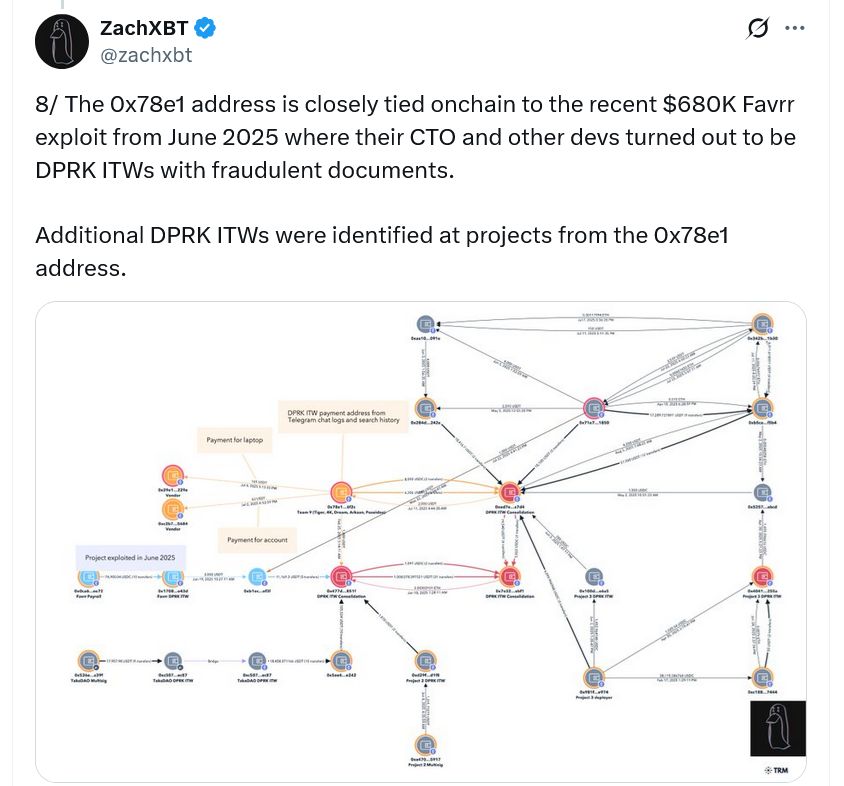 Source: ZachXBT
Source: ZachXBT
The evidence also provides insight into their areas of curiosity. One search asked whether ERC-20 tokens can be deployed on Solana, while another sought information on the top AI development companies in Europe.
Crypto firms need to do more due diligence
ZachXBT called on crypto and tech firms to do more homework on potential hirees — noting that many of these operations aren’t highly sophisticated, but the volume of applications often leads to hiring teams becoming negligent.
He added that a lack of collaboration between tech firms and freelance platforms further contributes to the problem.
Last month, the US Treasury took matters into its own hands, sanctioning two people and four entities involved in a North Korea-run IT worker ring infiltrating crypto firms.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
DOJ Exposes $7.8M Crypto Scam Tied To Bitcoin Rodney

Grayscale Signals Bitcoin Could Hit New Highs in 2026 Despite Recent Dip

Will the Bitcoin Cycle Survive American Monetary Policy?

