Embargo ransomware group moved $34M in crypto since April: TRM Labs
A relatively new ransomware group known as Embargo has become a key player in the cybercrime underground, moving over $34 million in crypto-linked ransom payments since April 2024.
Operating under a ransomware-as-a-service (RaaS) model, Embargo has hit critical infrastructure across the United States, with targets including hospitals and pharmaceutical networks, according to blockchain intelligence firm TRM Labs.
Victims include American Associated Pharmacies, Georgia-based Memorial Hospital and Manor, and Weiser Memorial Hospital in Idaho. Ransom demands have reportedly reached up to $1.3 million.
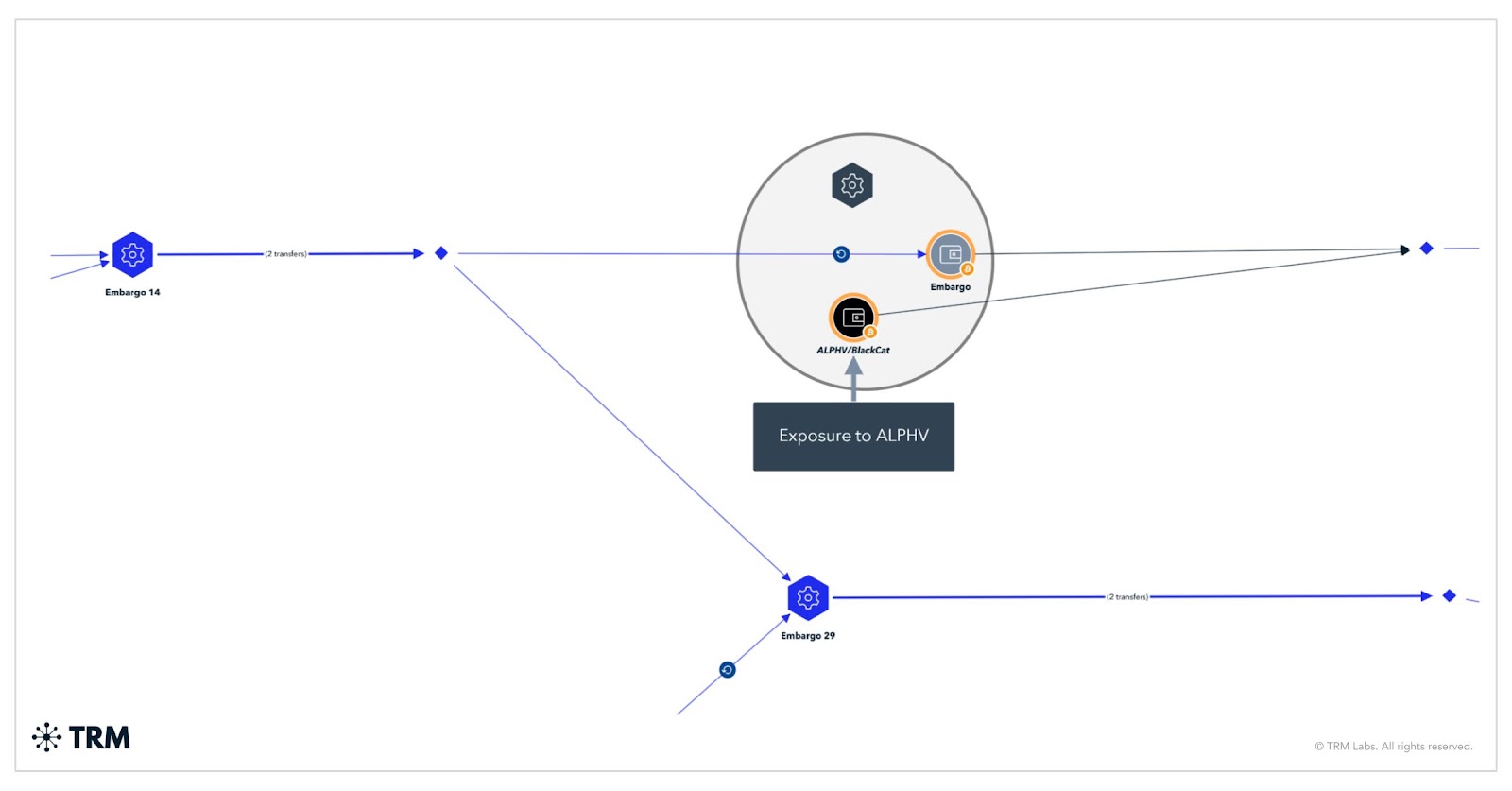
TRM's investigation suggests Embargo may be a rebranded version of the infamous BlackCat (ALPHV) operation, which disappeared following a suspected exit scam earlier this year. The two groups share technical overlap, using the Rust programming language, operating similar data leak sites, and exhibiting onchain ties through shared wallet infrastructure.
Related: US DOJ seizes $24M in crypto from accused Qakbot malware developer
Embargo holds $18.8M in dormant crypto
Around $18.8 million of Embargo’s crypto proceeds remain dormant in unaffiliated wallets, a tactic experts believe may be designed to delay detection or exploit better laundering conditions in the future.
The group uses a network of intermediary wallets, high-risk exchanges, and sanctioned platforms, including Cryptex.net, to obscure the origin of funds. From May through August, TRM traced at least $13.5 million across various virtual asset service providers and more than $1 million routed through Cryptex alone.
While not as visibly aggressive as LockBit or Cl0p, Embargo has adopted double extortion tactics, encrypting systems and threatening to leak sensitive data if victims fail to pay. In some instances, the group has publicly named individuals or leaked data on its site to increase pressure.
Embargo primarily targets sectors where downtime is costly, including healthcare, business services, and manufacturing, and has shown a preference for US-based victims, likely due to their higher capacity to pay.
Related: Coinbase faces $400M bill after insider phishing attack
UK to ban ransomware payments for public sector
The UK is set to ban ransomware payments for all public sector bodies and critical national infrastructure operators, including energy, healthcare, and local councils. The proposal introduces a prevention regime requiring victims outside the ban to report intended ransom payments.
The plan also includes a mandatory reporting system, with victims required to submit an initial report to the government within 72 hours of an attack and a detailed follow-up within 28 days.
Ransomware saw a 35% drop in attacks last year, according to Chainalysis. It marked the first drop in ransomware revenues since 2022, according to the report.
Magazine: Inside a 30,000 phone bot farm stealing crypto airdrops from real users
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Beyond Trading: A Look at Star New Projects and Major Updates in the Solana Ecosystem
The Solana Breakpoint 2025 conference was truly spectacular.

Quick Look at the 33 Winning Projects of the Solana Breakpoint 2025 Hackathon
Over 9,000 participants formed teams and submitted 1,576 projects, with a total of 33 projects winning awards. All of them are top industry seed projects selected from hundreds.

WEEX Labs: The Next Chapter for Memecoin, the Era of Flash Trends
In the era of rapid trends, memecoins have begun to shift from being a "joke" to becoming a "cultural index."

Aster launches Shield Mode: a protected high-performance trading mode for on-chain traders
Shield Mode is not merely an upgrade of a single feature, but rather part of Aster's broader vision.