Beware: SparkKitty malware wants your seed phrase screenshots
Cybersecurity firm Kaspersky has warned of a newly discovered malware known as SparkKitty, which steals photos from infected devices in the hopes of finding crypto seed phrases.
Kaspersky analysts Sergey Puzan and Dmitry Kalinin said in a report on Monday that SparkKitty is targeting both iOS and Android devices by infiltrating some of the apps on the Apple App Store and Google Play.
Once a device is infected, the malicious software indiscriminately steals all images in the photo gallery.
“Although we suspect the attackers’ main goal is to find screenshots of crypto wallet seed phrases, other sensitive data could also be present in the stolen images.”
Malicious apps focus on crypto themes
Two apps used to deliver the malware found by Kaspersky focused on crypto. One known as 币coin, which markets itself as a crypto information tracker , was on the App Store.
The second was SOEX, a messaging app with “crypto exchange features” on Google Play.
 SOEX is marketed as a messaging app with crypto exchange features. Source: Kaspersky
SOEX is marketed as a messaging app with crypto exchange features. Source: Kaspersky
“This app was uploaded to Google Play and installed over 10,000 times. We notified Google about it, and they removed the app from the store,” Puzan and Kalinin said.A Google spokesperson confirmed to Cointelegraph that the app had been removed from Google Play, and the developer was banned.
“Android users are automatically protected against this app regardless of download source by Google Play Protect, which is on by default on Android devices with Google Play Services,” the spokesperson said.
The Kaspersky analysts also discovered instances of SparkKitty being delivered through casino apps, adult-themed games and malicious TikTok clones.
SparkCat’s little brother
The malware is similar to SparkCat, which was identified during a Kaspersky investigation in January . The malware scans users’ pictures to find crypto wallet recovery phrases.
Both versions of the malware are likely from the same source, Puzan and Kalinin said, because they share similar features and include similar file paths from the attackers’ systems.
“While not technically or conceptually complex, this campaign has been ongoing since at least the beginning of 2024 and poses a significant threat to users,” Puzan and Kalinin said.
“Unlike the previously discovered SparkCat spyware, this malware isn’t picky about which photos it steals from the gallery.”
Southeast Asia and China main targets
The main targets of this malware campaign are users in Southeast Asia and China, based on Kaspersky’s findings, as the infected apps include various Chinese gambling games, TikTok and adult games.
“Judging by the distribution sources, this spyware primarily targets users in Southeast Asia and China,” Puzan and Kalinin said.
“However, it doesn’t have any technical limitations that would prevent it from attacking users in other regions,” they added.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
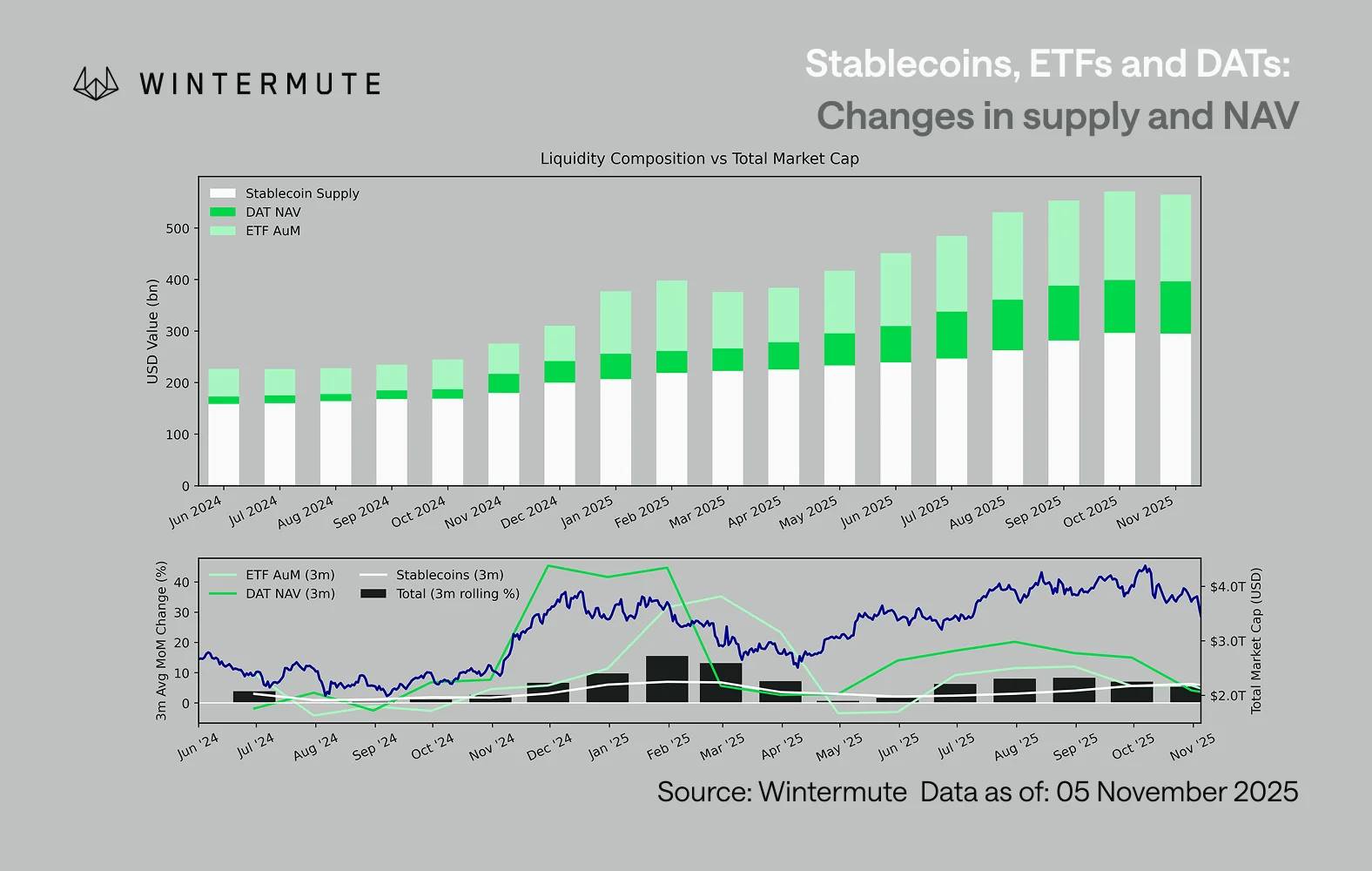
Wintermute: Liquidity, the Lifeline of the Crypto Industry, Is in Crisis
Liquidity determines every cryptocurrency cycle.
Ray Dalio's latest post: This time is different, the Federal Reserve is fueling a bubble
Because the fiscal side of government policy is now highly stimulative, quantitative easing will effectively monetize government debt, rather than simply reinjecting liquidity into the private system.

Famous Bitcoin bull "Cathie Wood" lowers target price due to the "replacement" by stablecoins
Cathie Wood has lowered her 2030 bitcoin bull market target price by about $300,000, after previously predicting it could reach $1.5 million.

Crypto: Balancer publishes a preliminary report on the hack that targeted it

